How it works :
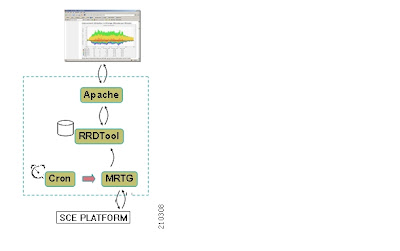 These are the components that will be used to install SNMP RTM:
These are the components that will be used to install SNMP RTM:
1. MRTG-2.1.5 - download from mrtg.org
2. rrdtool-1.2.15 - download from rrdtool.org
3. Active Perl 5.8 - search google.com and download
4. Apache2 - download from apache.org
5. sca_bb v3.1.6 - download from cisco.com
6. sca_bb utility - extracted from sca_bb v3.1.6
7. scabb_rtm_templates_v3.0.5A_b05 - download from cisco.com
8. firedaemon - search google.com and download
9. Java (jre) 1.4.2 - download from java.sun.com
- mrtg for collecting snmp
- rrd tool to store data
- Active perl for running mrtg
- Apache for running web server, cgi
- scabb v3.1.6 to get scabb utility
- scabb utility for generate mrtg cfg files
- scabb rtm template for generate cfg file refer to the template and sce configuration
- firedaemon for running scheduler
- java needs for running scabb utility
Getting started :
1. Install mrtg, perl, rrdtool in C:\
2. Install apache web-server C:\Program Files
3. Install firedaemon
4. Install java
5. Extract scabb v3.1.6, extract scabb util (bin & lib) to C:\
6. Extract scabb rtm template to C:\bin\
7. Create directory rtm-output in C:\bin\
8. Edit rtcmd.cfg file
#The absolute path to the RRD tool's execution files folder
#Use '\\' or '/' as path separator
rrdtool_bin_dir=C:/rrdtool-1.2.15/rrdtool/Release
#The absolute path where RTM files will be placed.
#This path will be used by MRTG to create and update the RRD files
#Note: path must not contain white spaces!
rtm_dir=C:/PROGRA~1/APACHE~1/Apache2.2/htdocs
#The absolute path to the MRTG bin folder.
#This path will be used to create file crontab.txt
mrtg_bin_dir=C:/mrtg-2.14.5/bin
#The SCE's community string
snmpCommunityString=public
rrdtool_bin_dir=C:/rrdtool-1.2.15/rrdtool/Release
9. Open command prompt, running this command "rtmcmd -S "ip_sce1;ipsce2" -U xxxxx -P xxxxx --pqb-sce=ip_sce1 --source-dir=/templates --dest-dir=/rtm-output -c ./rtmcmd.cfg
C:\bin\rtmcmd -S "ip_sce1;ipsce2" -U xxxxx -P xxxxx --pqb-sce=ip_sce1 --source-dir=/templates --dest-dir=/rtm-output -c ./rtmcmd.cfg
connecting to ip_sce1 ... done
retrieving service configuration from SCE ... done
disconnecting from device ... done
loading user configuration from file 'rtmcmd.cfg' ... done
processing templates from '\templates' to '\rtm-output' ... done
C:\bin>
10. Check rtm-output directory
C:\bin\rtm-output>dir
Volume in drive C has no label.
Volume Serial Number is C4C2-8BAA
Directory of C:\bin\rtm-output
08/31/2009 08:16 AM dir .
08/31/2009 08:16 AM dir ..
08/31/2009 10:30 AM 43 .htaccess
08/31/2009 10:30 AM 386 crontab-unix.txt
08/31/2009 10:30 AM 310 crontab-windows.txt
08/31/2009 08:16 AM dir mrtg-cfg
08/31/2009 08:16 AM dir sce_202.155.50.75
08/31/2009 08:16 AM dir sce_202.155.50.77
08/31/2009 08:16 AM dir static
11. Copy all file to C:\Program Files\Apache Software Foundation\Apache2.2\htdocs>
12. Edit httpd Apache configuration file and add this text :
Options Indexes FollowSymLinks ExecCGI
AllowOverride Indexes
Order allow,deny
Allow from all
13. Test mrtg and mrtg cfg file with this command :
C:\Perl\bin>perl.exe c:\mrtg-2.14.5\bin\mrtg "c:\Program Files\Apache Software Foundation\Apache2.2\htdocs\mrtg-cfg\ip_sce1_scabb_mrtg.cfg"
C:\Perl\bin>perl.exe c:\mrtg-2.14.5\bin\mrtg "c:\Program Files\Apache Software Foundation\Apache2.2\htdocs\mrtg-cfg\ip_sce1_scabb_mrtg.cfg"
If no error appear, you can check working directory a lot of rrd files has been generated.
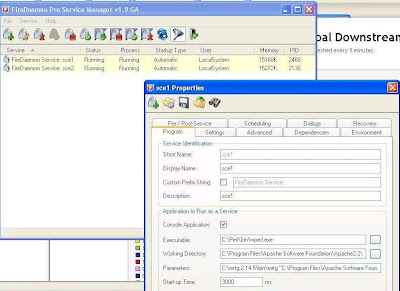
14. Open firedaemon, add new service definition :
Shortname : sce1
Executable : C:\Perl\bin\wperl.exe
Working Dir :C:\Program Files\Apache Software Foundation\Apache2.2\htdocs\sce_ip_sce1
Parameters : C:\mrtg-2.14.5\bin\mrtg "C:\Program Files\Apache Software Foundation\Apache2.2\htdocs\mrtg-cfg\ip_sce1_scabb_mrtg.cfg"
Start Service sce1
Shortname : sce2
Executable : C:\Perl\bin\wperl.exe
Working Dir :C:\Program Files\Apache Software Foundation\Apache2.2\htdocs\sce_ip_sce2
Parameters : C:\mrtg-2.14.5\bin\mrtg "C:\Program Files\Apache Software Foundation\Apache2.2\htdocs\mrtg-cfg\ip_sce2_scabb_mrtg.cfg"
Start service sce2
15. Open web browser and type :
http://localhost/sce_ip_sce1/
http://localhost/sce_ip_sce2/
And finally you will see the following display in your browser :
 Refference http://www.cisco.com/en/US/products/ps61/products_user_guide_book09186a0080843872.html
Refference http://www.cisco.com/en/US/products/ps61/products_user_guide_book09186a0080843872.html
 These are the components that will be used to install SNMP RTM:
These are the components that will be used to install SNMP RTM: 1. MRTG-2.1.5 - download from mrtg.org
2. rrdtool-1.2.15 - download from rrdtool.org
3. Active Perl 5.8 - search google.com and download
4. Apache2 - download from apache.org
5. sca_bb v3.1.6 - download from cisco.com
6. sca_bb utility - extracted from sca_bb v3.1.6
7. scabb_rtm_templates_v3.0.5A_b05 - download from cisco.com
8. firedaemon - search google.com and download
9. Java (jre) 1.4.2 - download from java.sun.com
- mrtg for collecting snmp
- rrd tool to store data
- Active perl for running mrtg
- Apache for running web server, cgi
- scabb v3.1.6 to get scabb utility
- scabb utility for generate mrtg cfg files
- scabb rtm template for generate cfg file refer to the template and sce configuration
- firedaemon for running scheduler
- java needs for running scabb utility
Getting started :
1. Install mrtg, perl, rrdtool in C:\
2. Install apache web-server C:\Program Files
3. Install firedaemon
4. Install java
5. Extract scabb v3.1.6, extract scabb util (bin & lib) to C:\
6. Extract scabb rtm template to C:\bin\
7. Create directory rtm-output in C:\bin\
8. Edit rtcmd.cfg file
#The absolute path to the RRD tool's execution files folder
#Use '\\' or '/' as path separator
rrdtool_bin_dir=C:/rrdtool-1.2.15/rrdtool/Release
#The absolute path where RTM files will be placed.
#This path will be used by MRTG to create and update the RRD files
#Note: path must not contain white spaces!
rtm_dir=C:/PROGRA~1/APACHE~1/Apache2.2/htdocs
#The absolute path to the MRTG bin folder.
#This path will be used to create file crontab.txt
mrtg_bin_dir=C:/mrtg-2.14.5/bin
#The SCE's community string
snmpCommunityString=public
rrdtool_bin_dir=C:/rrdtool-1.2.15/rrdtool/Release
9. Open command prompt, running this command "rtmcmd -S "ip_sce1;ipsce2" -U xxxxx -P xxxxx --pqb-sce=ip_sce1 --source-dir=/templates --dest-dir=/rtm-output -c ./rtmcmd.cfg
C:\bin\rtmcmd -S "ip_sce1;ipsce2" -U xxxxx -P xxxxx --pqb-sce=ip_sce1 --source-dir=/templates --dest-dir=/rtm-output -c ./rtmcmd.cfg
connecting to ip_sce1 ... done
retrieving service configuration from SCE ... done
disconnecting from device ... done
loading user configuration from file 'rtmcmd.cfg' ... done
processing templates from '\templates' to '\rtm-output' ... done
C:\bin>
10. Check rtm-output directory
C:\bin\rtm-output>dir
Volume in drive C has no label.
Volume Serial Number is C4C2-8BAA
Directory of C:\bin\rtm-output
08/31/2009 08:16 AM dir .
08/31/2009 08:16 AM dir ..
08/31/2009 10:30 AM 43 .htaccess
08/31/2009 10:30 AM 386 crontab-unix.txt
08/31/2009 10:30 AM 310 crontab-windows.txt
08/31/2009 08:16 AM dir mrtg-cfg
08/31/2009 08:16 AM dir sce_202.155.50.75
08/31/2009 08:16 AM dir sce_202.155.50.77
08/31/2009 08:16 AM dir static
11. Copy all file to C:\Program Files\Apache Software Foundation\Apache2.2\htdocs>
12. Edit httpd Apache configuration file and add this text :
Options Indexes FollowSymLinks ExecCGI
AllowOverride Indexes
Order allow,deny
Allow from all
13. Test mrtg and mrtg cfg file with this command :
C:\Perl\bin>perl.exe c:\mrtg-2.14.5\bin\mrtg "c:\Program Files\Apache Software Foundation\Apache2.2\htdocs\mrtg-cfg\ip_sce1_scabb_mrtg.cfg"
C:\Perl\bin>perl.exe c:\mrtg-2.14.5\bin\mrtg "c:\Program Files\Apache Software Foundation\Apache2.2\htdocs\mrtg-cfg\ip_sce1_scabb_mrtg.cfg"
If no error appear, you can check working directory a lot of rrd files has been generated.
14. Open firedaemon, add new service definition :
Shortname : sce1
Executable : C:\Perl\bin\wperl.exe
Working Dir :C:\Program Files\Apache Software Foundation\Apache2.2\htdocs\sce_ip_sce1
Parameters : C:\mrtg-2.14.5\bin\mrtg "C:\Program Files\Apache Software Foundation\Apache2.2\htdocs\mrtg-cfg\ip_sce1_scabb_mrtg.cfg"
Start Service sce1
Shortname : sce2
Executable : C:\Perl\bin\wperl.exe
Working Dir :C:\Program Files\Apache Software Foundation\Apache2.2\htdocs\sce_ip_sce2
Parameters : C:\mrtg-2.14.5\bin\mrtg "C:\Program Files\Apache Software Foundation\Apache2.2\htdocs\mrtg-cfg\ip_sce2_scabb_mrtg.cfg"
Start service sce2

15. Open web browser and type :
http://localhost/sce_ip_sce1/
http://localhost/sce_ip_sce2/
And finally you will see the following display in your browser :
 Refference http://www.cisco.com/en/US/products/ps61/products_user_guide_book09186a0080843872.html
Refference http://www.cisco.com/en/US/products/ps61/products_user_guide_book09186a0080843872.html




















