Nas-Port is one of the radius attribute that can be used for identifying user both of in the Router or in the radius server.
I'm using IOS SB and 7200 VXR for the router, it can be configured to send Nas-Port attribute or not. If you don't want to send it, you just configure the router like this :
Diagram : PC ----L3 ISG ----- INTERNET
|---- PORTAL
|---- RADIUS
-----------------------------------------------------------------------------------------------------------------
Configuration :
ISG-L4R(config)#aaa group server radius AAA
ISG-L4R(config-sg-radius)#attribute nas-port ?
format Set the format of the NAS-Port attribute
none Don't send nas-port attribute
ISG-L4R(config-sg-radius)#attribute nas-port none
The debug result will be like this :
(1). User login from Website :
006675: Apr 13 14:52:44 WIB: RADIUS: COA received from id 105 20.0.92.156:32775, CoA Request, len 93
006676: Apr 13 14:52:44 WIB: RADIUS/DECODE: VSA external len != internal + VSA hdr
(2). Nas-port is being disable :
006677: Apr 13 14:52:44 WIB: RADIUS/ENCODE(00000D42):Orig. component type = IEDGE_IP_SIP
006678: Apr 13 14:52:44 WIB: RADIUS/ENCODE: NAS PORT sending disabled
006679: Apr 13 14:52:44 WIB: RADIUS(00000D42): Config NAS IP: 10.0.4.101
006680: Apr 13 14:52:44 WIB: RADIUS/ENCODE(00000D42): acct_session_id: 3447
006681: Apr 13 14:52:44 WIB: RADIUS(00000D42): Config NAS IP: 10.0.4.101
(3). Login Request to Radius :
006682: Apr 13 14:52:44 WIB: RADIUS(00000D42): sending
006683: Apr 13 14:52:44 WIB: RADIUS(00000D42): Send Access-Request to 10.0.100.29:1645 id 1645/150, len 109
006684: Apr 13 14:52:44 WIB: RADIUS: authenticator C0 6E 4D 8F 2E 5B 9B 17 - 89 90 06 DE 9F C4 CB B2
006685: Apr 13 14:52:44 WIB: RADIUS: Framed-IP-Address [8] 6 30.0.74.1
006686: Apr 13 14:52:44 WIB: RADIUS: User-Name [1] 11 "pedi128k"
006687: Apr 13 14:52:44 WIB: RADIUS: User-Password [2] 18 *
006688: Apr 13 14:52:44 WIB: RADIUS: NAS-Port-Type [61] 6 Virtual [5]
006689: Apr 13 14:52:44 WIB: RADIUS: NAS-Port-Id [87] 11 "0/0/3/806"
006690: Apr 13 14:52:44 WIB: RADIUS: Service-Type [6] 6 Login [1]
006691: Apr 13 14:52:44 WIB: RADIUS: NAS-IP-Address [4] 6 10.0.4.101
006692: Apr 13 14:52:44 WIB: RADIUS: Acct-Session-Id [44] 10 "00000D77"
006693: Apr 13 14:52:44 WIB: RADIUS: Nas-Identifier [32] 9 "ISG-L4R"
006694: Apr 13 14:52:44 WIB: RADIUS: Event-Timestamp [55] 6 1239609164
(4). Received response from Radius :
006695: Apr 13 14:52:45 WIB: RADIUS: Received from id 1645/150 10.0.100.29:1645, Access-Accept, len 94
006696: Apr 13 14:52:45 WIB: RADIUS: authenticator 28 0C 18 47 8A E5 4E 9C - 45 7F B6 21 70 E0 A3 F0
006697: Apr 13 14:52:45 WIB: RADIUS: Class [25] 50
006698: Apr 13 14:52:45 WIB: RADIUS: 53 42 52 2D 43 4C 20 44 4E 3D 22 63 61 62 6C 65 [SBR-CL DN="pedi]
006699: Apr 13 14:52:45 WIB: RADIUS: 31 32 38 6B 22 20 41 54 3D 22 32 30 30 22 20 55 [128k" AT="200" U]
006700: Apr 13 14:52:45 WIB: RADIUS: 53 3D 22 22 20 53 49 3D 22 32 31 35 32 32 22 00 [ S="" SI="21522"]
006701: Apr 13 14:52:45 WIB: RADIUS: Vendor, Unknown [26] 12
006702: Apr 13 14:52:45 WIB: RADIUS: Unsupported [2] 6
006703: Apr 13 14:52:45 WIB: RADIUS: 00 00 00 01
006704: Apr 13 14:52:45 WIB: RADIUS: Session-Timeout [27] 6 86400
006705: Apr 13 14:52:45 WIB: RADIUS: Idle-Timeout [28] 6 300
006706: Apr 13 14:52:45 WIB: RADIUS(00000D42): Received from id 1645/150
006707: Apr 13 14:52:45 WIB: RADIUS/ENCODE(00000D42):Orig. component type = IEDGE_IP_SIP
006708: Apr 13 14:52:45 WIB: RADIUS: AAA Unsupported Attr: timeout [371] 4 86400
006709: Apr 13 14:52:45 WIB: RADIUS: AAA Unsupported Attr: idletime [123] 4 300
(6). Ack response to Portal :
006710: Apr 13 14:52:45 WIB: RADIUS(00000D42): sending
006711: Apr 13 14:52:45 WIB: RADIUS(00000D42): Send CoA Ack Response to 20.0.92.156:32775 id 105, len 70
006712: Apr 13 14:52:45 WIB: RADIUS: authenticator 55 36 45 5F 9E 23 1E 37 - 0E 07 E7 29 2B FD 0B 16
006713: Apr 13 14:52:45 WIB: RADIUS: Vendor, Cisco [26] 18
006714: Apr 13 14:52:45 WIB: RADIUS: ssg-command-code [252] 12
006715: Apr 13 14:52:45 WIB: RADIUS: 01 63 61 62 6C 65 31 32 38 6B [Account-Log-On pedi128k]
006716: Apr 13 14:52:45 WIB: RADIUS: Vendor, Cisco [26] 20
006717: Apr 13 14:52:45 WIB: RADIUS: ssg-account-info [250] 14 "S30.0.74.1"
006718: Apr 13 14:52:45 WIB: RADIUS: Session-Timeout [27] 6 86400
006719: Apr 13 14:52:45 WIB: RADIUS: Idle-Timeout [28] 6 300
006720: Apr 13 14:52:45 WIB: RADIUS/ENCODE(00000D42):Orig. component type = IEDGE_IP_SIP
006721: Apr 13 14:52:45 WIB: RADIUS/ENCODE: NAS PORT sending disabled
006722: Apr 13 14:52:45 WIB: RADIUS(00000D42): Config NAS IP: 10.0.4.101
006723: Apr 13 14:52:45 WIB: RADIUS(00000D42): Config NAS IP: 10.0.4.101
(7). Sending Accounting Request :
006724: Apr 13 14:52:45 WIB: RADIUS(00000D42): sending
006725: Apr 13 14:52:45 WIB: RADIUS(00000D42): Send Accounting-Request to 10.0.100.29:1646 id 1646/64, len 206
006726: Apr 13 14:52:45 WIB: RADIUS: authenticator D4 A8 64 DC B7 6B 89 1B - C9 D8 3B AF 45 53 03 0D
006727: Apr 13 14:52:45 WIB: RADIUS: Acct-Session-Id [44] 10 "00000D79"
006728: Apr 13 14:52:45 WIB: RADIUS: Framed-Protocol [7] 6 PPP [1]
006729: Apr 13 14:52:45 WIB: RADIUS: Vendor, Cisco [26] 13
006730: Apr 13 14:52:45 WIB: RADIUS: ssg-service-info [251] 7 "NINET"
006731: Apr 13 14:52:45 WIB: RADIUS: Vendor, Cisco [26] 34
006732: Apr 13 14:52:45 WIB: RADIUS: Cisco AVpair [1] 28 "parent-session-id=00000D77"
006733: Apr 13 14:52:45 WIB: RADIUS: User-Name [1] 11 "pedi128k"
006734: Apr 13 14:52:45 WIB: RADIUS: Acct-Status-Type [40] 6 Start [1]
006735: Apr 13 14:52:45 WIB: RADIUS: Framed-IP-Address [8] 6 30.0.74.1
006736: Apr 13 14:52:45 WIB: RADIUS: NAS-Port-Type [61] 6 Virtual [5]
006737: Apr 13 14:52:45 WIB: RADIUS: NAS-Port-Id [87] 11 "0/0/3/806"
006738: Apr 13 14:52:45 WIB: RADIUS: Class [25] 50
006739: Apr 13 14:52:45 WIB: RADIUS: 53 42 52 2D 43 4C 20 44 4E 3D 22 63 61 62 6C 65 [SBR-CL DN="pedi]
006740: Apr 13 14:52:45 WIB: RADIUS: 31 32 38 6B 22 20 41 54 3D 22 32 30 30 22 20 55 [128k" AT="200" U]
006741: Apr 13 14:52:45 WIB: RADIUS: 53 3D 22 22 20 53 49 3D 22 32 31 35 32 32 22 00 [ S="" SI="21522"]
006742: Apr 13 14:52:45 WIB: RADIUS: Service-Type [6] 6 Framed [2]
006743: Apr 13 14:52:45 WIB: RADIUS: NAS-IP-Address [4] 6 10.0.4.101
006744: Apr 13 14:52:45 WIB: RADIUS: Event-Timestamp [55] 6 1239609165
006745: Apr 13 14:52:45 WIB: RADIUS: Nas-Identifier [32] 9 "ISG-L4R"
006746: Apr 13 14:52:45 WIB: RADIUS: Acct-Delay-Time [41] 6 0
(8). Received accounting response from Radius :
006747: Apr 13 14:52:45 WIB: RADIUS: Received from id 1646/64 10.0.100.29:1646, Accounting-response, len 20
In the above debug output you can see that there are no Nas-Port send in the user authentication and accounting. It because Nas-Port sending is being disabled.
-----------------------------------------------------------------------------------------------------------------
In this topology I use ip routed session scenario, in this scenario we can see Router (ISG) is sending the Nas-Port value equal to zero.
Here is the sample debug of nas port equal to zero :
(1). Sending Authentication request to Radius :
001672: Apr 13 12:33:27 WIB: RADIUS(00000A4B): Send Access-Request to 10.0.100.29:1645 id 1645/60, len 116
001673: Apr 13 12:33:27 WIB: RADIUS: authenticator 0A 4D 6D A0 9A 89 A0 E8 - 2D 70 65 89 25 90 2F 3A
001674: Apr 13 12:33:27 WIB: RADIUS: Framed-IP-Address [8] 6 30.0.74.1
001675: Apr 13 12:33:27 WIB: RADIUS: User-Name [1] 12 "pedi1024k"
001676: Apr 13 12:33:27 WIB: RADIUS: User-Password [2] 18 *
001677: Apr 13 12:33:27 WIB: RADIUS: NAS-Port-Type [61] 6 Virtual [5]
001678: Apr 13 12:33:27 WIB: RADIUS: NAS-Port [5] 6 0
001679: Apr 13 12:33:27 WIB: RADIUS: NAS-Port-Id [87] 11 "0/0/3/806"
001680: Apr 13 12:33:27 WIB: RADIUS: Service-Type [6] 6 Login [1]
001681: Apr 13 12:33:27 WIB: RADIUS: NAS-IP-Address [4] 6 10.0.4.101
001682: Apr 13 12:33:27 WIB: RADIUS: Acct-Session-Id [44] 10 "00000A4B"
001683: Apr 13 12:33:27 WIB: RADIUS: Nas-Identifier [32] 9 "ISG-L4R"
001684: Apr 13 12:33:27 WIB: RADIUS: Event-Timestamp [55] 6 1239600807
(2). Received Authentication Response from Radius :
001685: Apr 13 12:33:27 WIB: RADIUS: Received from id 1645/60 10.0.100.29:1645, Access-Accept, len 95
001686: Apr 13 12:33:27 WIB: RADIUS: authenticator 95 38 A5 67 3E 35 7A B2 - 50 AE 7B F8 2B 0B B3 64
001687: Apr 13 12:33:27 WIB: RADIUS: Class [25] 51
001688: Apr 13 12:33:27 WIB: RADIUS: 53 42 52 2D 43 4C 20 44 4E 3D 22 63 61 62 6C 65 [SBR-CL DN="pedi]
001689: Apr 13 12:33:27 WIB: RADIUS: 31 30 32 34 6B 22 20 41 54 3D 22 32 30 30 22 20 [1024k" AT="200" ]
001690: Apr 13 12:33:27 WIB: RADIUS: 55 53 3D 22 22 20 53 49 3D 22 32 31 34 38 32 22 [US="" SI="21482"]
001691: Apr 13 12:33:27 WIB: RADIUS: 00
001692: Apr 13 12:33:27 WIB: RADIUS: Vendor, Unknown [26] 12
001693: Apr 13 12:33:27 WIB: RADIUS: Unsupported [2] 6
001694: Apr 13 12:33:27 WIB: RADIUS: 00 00 00 01
001695: Apr 13 12:33:27 WIB: RADIUS: Session-Timeout [27] 6 86400
001696: Apr 13 12:33:27 WIB: RADIUS: Idle-Timeout [28] 6 300
001697: Apr 13 12:33:27 WIB: RADIUS(00000A4B): Received from id 1645/60
001698: Apr 13 12:33:27 WIB: RADIUS/ENCODE(00000A4B):Orig. component type = IEDGE_IP_SIP
001699: Apr 13 12:33:27 WIB: RADIUS: AAA Unsupported Attr: timeout [371] 4 86400
001700: Apr 13 12:33:27 WIB: RADIUS: AAA Unsupported Attr: idletime [123] 4 300
(3) Sending Ack response to portal :
001701: Apr 13 12:33:27 WIB: RADIUS(00000A4B): sending
001702: Apr 13 12:33:27 WIB: RADIUS(00000A4B): Send CoA Ack Response to 20.0.92.156:32775 id 44, len 71
001703: Apr 13 12:33:27 WIB: RADIUS: authenticator 67 B9 4E 33 4C D6 D9 B3 - 7B D4 95 75 6B AF F0 95
001704: Apr 13 12:33:27 WIB: RADIUS: Vendor, Cisco [26] 19
001705: Apr 13 12:33:27 WIB: RADIUS: ssg-command-code [252] 13
001706: Apr 13 12:33:27 WIB: RADIUS: 01 63 61 62 6C 65 31 30 32 34 6B [Account-Log-On cable1024k]
001707: Apr 13 12:33:27 WIB: RADIUS: Vendor, Cisco [26] 20
001708: Apr 13 12:33:27 WIB: RADIUS: ssg-account-info [250] 14 "S30.0.74.1"
001709: Apr 13 12:33:27 WIB: RADIUS: Session-Timeout [27] 6 86400
001710: Apr 13 12:33:27 WIB: RADIUS: Idle-Timeout [28] 6 300
001711: Apr 13 12:33:27 WIB: RADIUS/ENCODE(00000A4B):Orig. component type = IEDGE_IP_SIP
001712: Apr 13 12:33:27 WIB: RADIUS(00000A4B): Config NAS IP: 10.0.4.101
001713: Apr 13 12:33:27 WIB: RADIUS(00000A4B): Config NAS IP: 10.0.4.101
(4). Sending Accounting request to Radius :
001714: Apr 13 12:33:27 WIB: RADIUS(00000A4B): sending
001715: Apr 13 12:33:27 WIB: RADIUS(00000A4B): Send Accounting-Request to 10.0.100.29:1646 id 1646/11, len 214
001716: Apr 13 12:33:27 WIB: RADIUS: authenticator 2C 90 A8 7A 46 99 3C 70 - BE 6D F7 25 21 19 4F C9
001717: Apr 13 12:33:27 WIB: RADIUS: Acct-Session-Id [44] 10 "00000A4F"
001718: Apr 13 12:33:27 WIB: RADIUS: Framed-Protocol [7] 6 PPP [1]
001719: Apr 13 12:33:27 WIB: RADIUS: Vendor, Cisco [26] 13
001720: Apr 13 12:33:27 WIB: RADIUS: ssg-service-info [251] 7 "NINET"
001721: Apr 13 12:33:27 WIB: RADIUS: Vendor, Cisco [26] 34
001722: Apr 13 12:33:27 WIB: RADIUS: Cisco AVpair [1] 28 "parent-session-id=00000A4B"
001723: Apr 13 12:33:27 WIB: RADIUS: User-Name [1] 12 "pedi1024k"
001724: Apr 13 12:33:27 WIB: RADIUS: Acct-Status-Type [40] 6 Start [1]
001725: Apr 13 12:33:27 WIB: RADIUS: Framed-IP-Address [8] 6 30.0.74.1
001726: Apr 13 12:33:27 WIB: RADIUS: NAS-Port-Type [61] 6 Virtual [5]
001727: Apr 13 12:33:27 WIB: RADIUS: NAS-Port [5] 6 0
001728: Apr 13 12:33:27 WIB: RADIUS: NAS-Port-Id [87] 11 "0/0/3/806"
001729: Apr 13 12:33:27 WIB: RADIUS: Class [25] 51
001730: Apr 13 12:33:27 WIB: RADIUS: 53 42 52 2D 43 4C 20 44 4E 3D 22 63 61 62 6C 65 [SBR-CL DN="pedi]
001731: Apr 13 12:33:27 WIB: RADIUS: 31 30 32 34 6B 22 20 41 54 3D 22 32 30 30 22 20 [1024k" AT="200" ]
001732: Apr 13 12:33:27 WIB: RADIUS: 55 53 3D 22 22 20 53 49 3D 22 32 31 34 38 32 22 [US="" SI="21482"]
001733: Apr 13 12:33:27 WIB: RADIUS: 00
001734: Apr 13 12:33:27 WIB: RADIUS: Service-Type [6] 6 Framed [2]
001735: Apr 13 12:33:27 WIB: RADIUS: NAS-IP-Address [4] 6 10.0.4.101
001736: Apr 13 12:33:27 WIB: RADIUS: Event-Timestamp [55] 6 1239600807
001737: Apr 13 12:33:27 WIB: RADIUS: Nas-Identifier [32] 9 "ISG-L4R"
001738: Apr 13 12:33:27 WIB: RADIUS: Acct-Delay-Time [41] 6 0
(4). Received Accounting Response from Radius :
001739: Apr 13 12:33:28 WIB: RADIUS: Received from id 1646/11 10.0.100.29:1646, Accounting-response, len 20
-----------------------------------------------------------------------------------------------------------------
And if you want to make nas-port not equal to zero, you can use extended Nas-port support.
Configuration :
aaa group server radius AAA
server 10.0.100.29 auth-port 1645 acct-port 1646
ip radius source-interface GigabitEthernet0/3.806
attribute nas-port format e UUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUU
deadtime 10
and the result will be like this :
(1). User login at portal :
007259: Apr 13 15:07:39 WIB: RADIUS: COA received from id 122 20.0.92.156:32775, CoA Request, len 95
007260: Apr 13 15:07:39 WIB: RADIUS/DECODE: VSA external len != internal + VSA hdr
007261: Apr 13 15:07:39 WIB: RADIUS/ENCODE(00000D81):Orig. component type = IEDGE_IP_SIP
007262: Apr 13 15:07:39 WIB: RADIUS: Format E value 0xDBD for character U with bitmask 0xFFFFFFFF
007263: Apr 13 15:07:39 WIB: RADIUS: Format E port 0xDBD with bit 32 processed
007264: Apr 13 15:07:39 WIB: RADIUS(00000D81): Config NAS IP: 10.0.4.101
007265: Apr 13 15:07:39 WIB: RADIUS/ENCODE(00000D81): acct_session_id: 3517
007266: Apr 13 15:07:39 WIB: RADIUS(00000D81): Config NAS IP: 10.0.4.101
007267: Apr 13 15:07:39 WIB: RADIUS(00000D81): sending
(2). Sending Authentication Request to Radius :
007268: Apr 13 15:07:39 WIB: RADIUS(00000D81): Send Access-Request to 10.0.100.29:1645 id 1645/158, len 116
007269: Apr 13 15:07:39 WIB: RADIUS: authenticator 89 50 7C 69 43 3C D1 EE - 65 30 C4 22 B1 6A 38 65
007270: Apr 13 15:07:39 WIB: RADIUS: Framed-IP-Address [8] 6 30.0.74.3
007271: Apr 13 15:07:39 WIB: RADIUS: User-Name [1] 12 "pedi1024k"
007272: Apr 13 15:07:39 WIB: RADIUS: User-Password [2] 18 *
007273: Apr 13 15:07:39 WIB: RADIUS: NAS-Port-Type [61] 6 Ethernet [15]
007274: Apr 13 15:07:39 WIB: RADIUS: NAS-Port [5] 6 3517
007275: Apr 13 15:07:39 WIB: RADIUS: NAS-Port-Id [87] 11 "0/0/3/806"
007276: Apr 13 15:07:39 WIB: RADIUS: Service-Type [6] 6 Login [1]
007277: Apr 13 15:07:39 WIB: RADIUS: NAS-IP-Address [4] 6 10.0.4.101
007278: Apr 13 15:07:39 WIB: RADIUS: Acct-Session-Id [44] 10 "00000DBD"
007279: Apr 13 15:07:39 WIB: RADIUS: Nas-Identifier [32] 9 "ISG-L4R"
007280: Apr 13 15:07:39 WIB: RADIUS: Event-Timestamp [55] 6 1239610059
(3). Received Response from Radius :
007281: Apr 13 15:07:39 WIB: RADIUS: Received from id 1645/158 10.0.100.29:1645, Access-Accept, len 95
007282: Apr 13 15:07:39 WIB: RADIUS: authenticator E3 22 CC 82 6E 49 F3 20 - 9C 20 5E CE 7D B9 EF 45
007283: Apr 13 15:07:39 WIB: RADIUS: Class [25] 51
007284: Apr 13 15:07:39 WIB: RADIUS: 53 42 52 2D 43 4C 20 44 4E 3D 22 63 61 62 6C 65 [SBR-CL DN="pedi]
007285: Apr 13 15:07:39 WIB: RADIUS: 31 30 32 34 6B 22 20 41 54 3D 22 32 30 30 22 20 [1024k" AT="200" ]
007286: Apr 13 15:07:39 WIB: RADIUS: 55 53 3D 22 22 20 53 49 3D 22 32 31 35 32 35 22 [US="" SI="21525"]
007287: Apr 13 15:07:39 WIB: RADIUS: 00
007288: Apr 13 15:07:39 WIB: RADIUS: Vendor, Unknown [26] 12
007289: Apr 13 15:07:39 WIB: RADIUS: Unsupported [2] 6
007290: Apr 13 15:07:39 WIB: RADIUS: 00 00 00 01
007291: Apr 13 15:07:39 WIB: RADIUS: Session-Timeout [27] 6 86400
007292: Apr 13 15:07:39 WIB: RADIUS: Idle-Timeout [28] 6 300
007293: Apr 13 15:07:39 WIB: RADIUS(00000D81): Received from id 1645/158
007294: Apr 13 15:07:39 WIB: RADIUS/ENCODE(00000D81):Orig. component type = IEDGE_IP_SIP
007295: Apr 13 15:07:39 WIB: RADIUS: AAA Unsupported Attr: timeout [371] 4 86400
007296: Apr 13 15:07:39 WIB: RADIUS: AAA Unsupported Attr: idletime [123] 4 300
(4). Sending Ack response to portal :
007297: Apr 13 15:07:39 WIB: RADIUS(00000D81): sending
007298: Apr 13 15:07:39 WIB: RADIUS(00000D81): Send CoA Ack Response to 20.0.92.156:32775 id 122, len 71
007299: Apr 13 15:07:39 WIB: RADIUS: authenticator D0 0B D7 83 04 4F 32 6A - 87 17 3C 62 0D 1E 25 64
007300: Apr 13 15:07:39 WIB: RADIUS: Vendor, Cisco [26] 19
007301: Apr 13 15:07:39 WIB: RADIUS: ssg-command-code [252] 13
007302: Apr 13 15:07:39 WIB: RADIUS: 01 63 61 62 6C 65 31 30 32 34 6B [Account-Log-On pedi1024k]
007303: Apr 13 15:07:39 WIB: RADIUS: Vendor, Cisco [26] 20
007304: Apr 13 15:07:39 WIB: RADIUS: ssg-account-info [250] 14 "S30.0.74.3"
007305: Apr 13 15:07:39 WIB: RADIUS: Session-Timeout [27] 6 86400
007306: Apr 13 15:07:39 WIB: RADIUS: Idle-Timeout [28] 6 300
007307: Apr 13 15:07:39 WIB: RADIUS/ENCODE(00000D81):Orig. component type = IEDGE_IP_SIP
007308: Apr 13 15:07:39 WIB: RADIUS: Format E value 0xDBD for character U with bitmask 0xFFFFFFFF
007309: Apr 13 15:07:39 WIB: RADIUS: Format E port 0xDBD with bit 32 processed
007310: Apr 13 15:07:39 WIB: RADIUS(00000D81): Config NAS IP: 10.0.4.101
007311: Apr 13 15:07:39 WIB: RADIUS(00000D81): Config NAS IP: 10.0.4.101
007312: Apr 13 15:07:39 WIB: RADIUS(00000D81): sending
(5). Sending Accounting Request to Radius :
007313: Apr 13 15:07:39 WIB: RADIUS(00000D81): Send Accounting-Request to 10.0.100.29:1646 id 1646/72, len 214
007314: Apr 13 15:07:39 WIB: RADIUS: authenticator 0B 51 C5 1E 61 E2 2F 15 - E2 8A 31 51 10 86 5E 63
007315: Apr 13 15:07:39 WIB: RADIUS: Acct-Session-Id [44] 10 "00000DBF"
007316: Apr 13 15:07:39 WIB: RADIUS: Framed-Protocol [7] 6 PPP [1]
007317: Apr 13 15:07:39 WIB: RADIUS: Vendor, Cisco [26] 13
007318: Apr 13 15:07:39 WIB: RADIUS: ssg-service-info [251] 7 "NINET"
007319: Apr 13 15:07:39 WIB: RADIUS: Vendor, Cisco [26] 34
007320: Apr 13 15:07:39 WIB: RADIUS: Cisco AVpair [1] 28 "parent-session-id=00000DBD"
007321: Apr 13 15:07:39 WIB: RADIUS: User-Name [1] 12 "pedi1024k"
007322: Apr 13 15:07:39 WIB: RADIUS: Acct-Status-Type [40] 6 Start [1]
007323: Apr 13 15:07:39 WIB: RADIUS: Framed-IP-Address [8] 6 30.0.74.3
007324: Apr 13 15:07:39 WIB: RADIUS: NAS-Port-Type [61] 6 Ethernet [15]
007325: Apr 13 15:07:39 WIB: RADIUS: NAS-Port [5] 6 3517
007326: Apr 13 15:07:39 WIB: RADIUS: NAS-Port-Id [87] 11 "0/0/3/806"
007327: Apr 13 15:07:39 WIB: RADIUS: Class [25] 51
007328: Apr 13 15:07:39 WIB: RADIUS: 53 42 52 2D 43 4C 20 44 4E 3D 22 63 61 62 6C 65 [SBR-CL DN="pedi]
007329: Apr 13 15:07:39 WIB: RADIUS: 31 30 32 34 6B 22 20 41 54 3D 22 32 30 30 22 20 [1024k" AT="200" ]
007330: Apr 13 15:07:39 WIB: RADIUS: 55 53 3D 22 22 20 53 49 3D 22 32 31 35 32 35 22 [US="" SI="21525"]
007331: Apr 13 15:07:39 WIB: RADIUS: 00
007332: Apr 13 15:07:39 WIB: RADIUS: Service-Type [6] 6 Framed [2]
007333: Apr 13 15:07:39 WIB: RADIUS: NAS-IP-Address [4] 6 10.0.4.101
007334: Apr 13 15:07:39 WIB: RADIUS: Event-Timestamp [55] 6 1239610059
007335: Apr 13 15:07:39 WIB: RADIUS: Nas-Identifier [32] 9 "ISG-L4R"
007336: Apr 13 15:07:39 WIB: RADIUS: Acct-Delay-Time [41] 6 0
(6). Received Accounting Response from Radius :
007337: Apr 13 15:07:39 WIB: RADIUS: Received from id 1646/72 10.0.100.29:1646, Accounting-response, len 20
In the above configuration is using format 'e' Nas-Port, format e is customized instead of format a to c, it is developed because not all off format are supported in the new cisco platform.
What i'm using in the configruration for the format nas-port is session id "U"
Radius-server attribute nas-port format
The value of session-id (hexadecimal) is converted to nas-port value (decimal)
Here is the result :
007320: Apr 13 15:07:39 WIB: RADIUS: Cisco AVpair [1] 28 "parent-session-id=00000DBD"
Ox 00000DBD = 3517
You can find the detail from this cisco site
http://www.cisco.com/en/US/docs/ios/12_2sb/feature/guide/rd_naspt.html
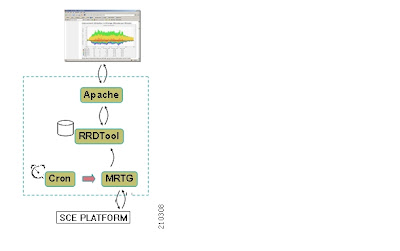 These are the components that will be used to install SNMP RTM:
These are the components that will be used to install SNMP RTM: 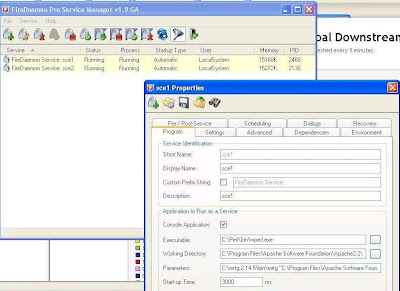
 Refference http://www.cisco.com/en/US/products/ps61/products_user_guide_book09186a0080843872.html
Refference http://www.cisco.com/en/US/products/ps61/products_user_guide_book09186a0080843872.html





















